Security Model
Vision 3 security uses a hierarchical model to represent the individual modules. Think of this model as a tree (albeit, upside-down). The root of the tree is the module itself, for example, Consultation Manager. When we expand the root, we see other functions within the module. If these functions can also be expanded, they are called branches, if they cannot, we call them leaves.
Groups and users added at the root have access to all parts of the tree. This is for convenience, so you do not have to define what parts of a module a group can or cannot access.
Groups added to branches or leaves have access granted by their position in the tree. The first level of branches from the root is the least secure, and the leaves are the highest.
For example, if you expand Consultation Manager, a group of Clinical Managers displays, they can access all functions within Consultation Manager. There is a further option of Read Only, this is the lowest category of security, someone who can look at Consultation Manager but not make any entries:

Once again, you can select Expand  to expand the list further:
to expand the list further:
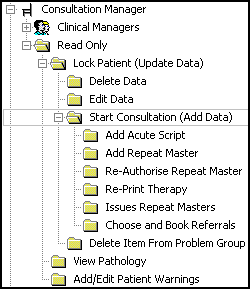
The default is illustrated above for Consultation Manager, where the Clinical Managers group is in the immediate level beneath the Consultation Manager heading giving all Clinical Managers all rights.
Visualise the tree being upside-down, the root being Consultation Manager.
The users or groups here have access to all of Consultation Manager, the root represents the least secure access. The leaves are the most secure access to the module:
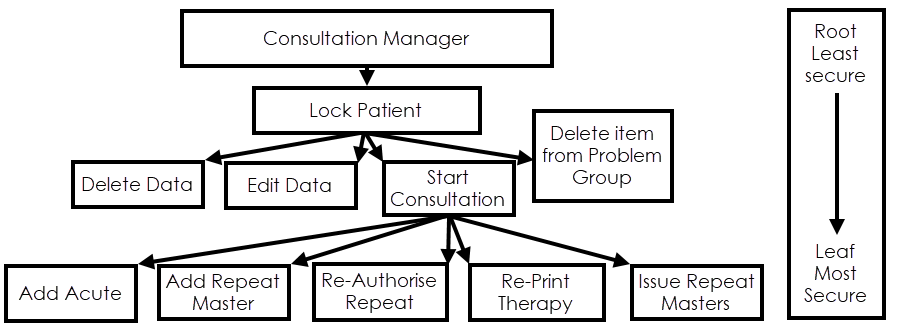
A path traversing the tree from the root to a leaf moves through increasing access restriction, from the least secure at the first branch to the most secure at the leaf. Paths in the tree are set so that rights follow system logic.
For example, to delete data we must first lock the relevant patient record, so Delete Data is a leaf of the Lock Patient.
Users added at the root are given access to everything within the tree. This all rights permission granted at the node are checked first. If a user or group is found here, then they are assumed to have all rights and checking stops.
If a user is not found at the root, checking begins at the first level of the tree. Groups or users found here are assumed to have incremental rights.
Incremental rights grant permissions to all leaves between the branch to which the group or user is added and the root, but a group or user is refused access to anything in its sub-tree. The permissions of a group or user are determined by the path that is traced between it and the root. Permissions only apply to the path from the leaf to the root; they do not include any other leaves on that level.
For example, a group or user added at the Lock Patient leaf would have access to Lock Patient and Consultation Manager, but not to other leaves.
A group or user added to Start Consultation would have access to Start Consultation, Lock Patient, and Consultation Manager, but not to Delete Data, Edit Data, Delete from Problem Group, which are on the same level but not on the branch.